
Elliptic Curve Diffie-Hellman (ECDH) Key Exchange Protocol. Two users,... | Download Scientific Diagram
GitHub - elesiuta/ECDH: Elliptic-curve Diffie–Hellman key exchange in the binary finite field (GF(2^n))

Figure 2 from Performance analysis of point multiplication algorithms in ECDH for an end-to-end VoIP network | Semantic Scholar

The Security Buddy on Twitter: "How does Elliptic Curve Cryptography work? https://t.co/f6k3Mbb0ls #security #encryption #ECDH https://t.co/z6uYu73g32" / Twitter


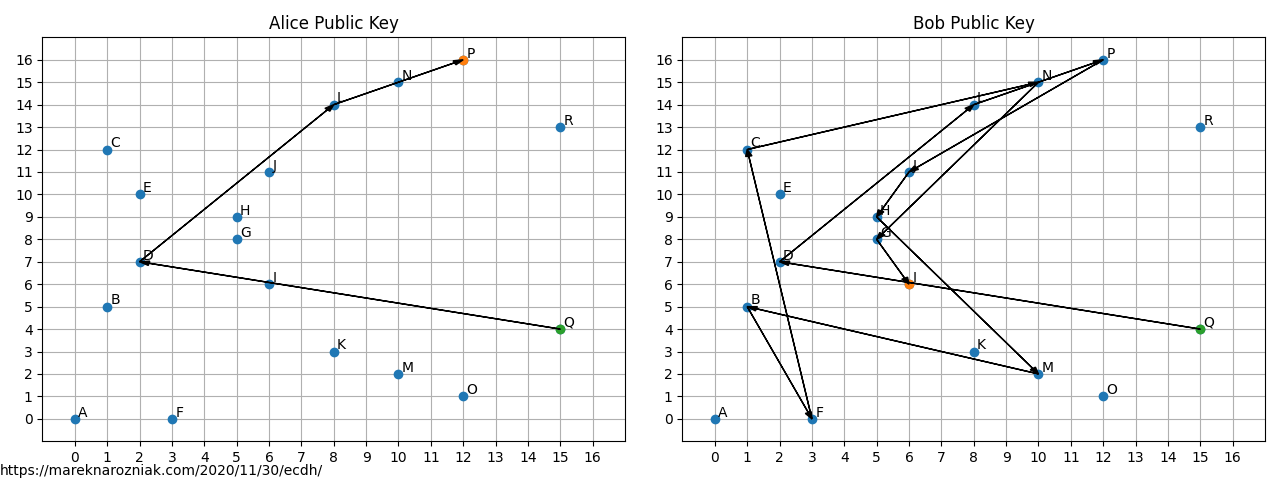
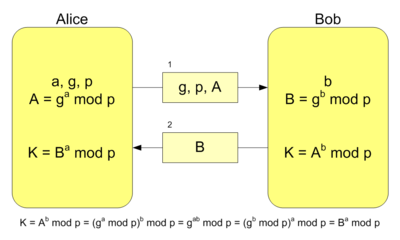
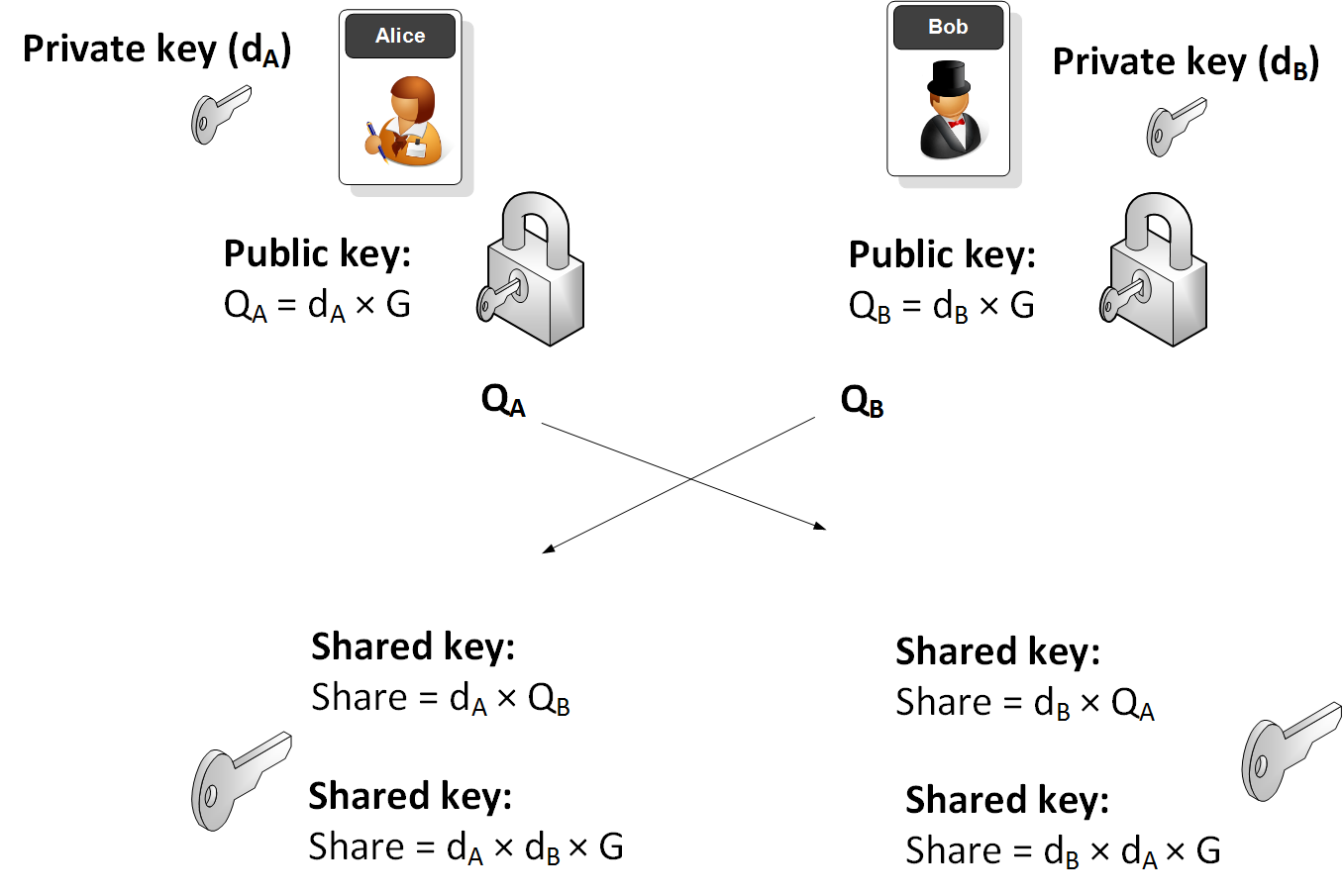

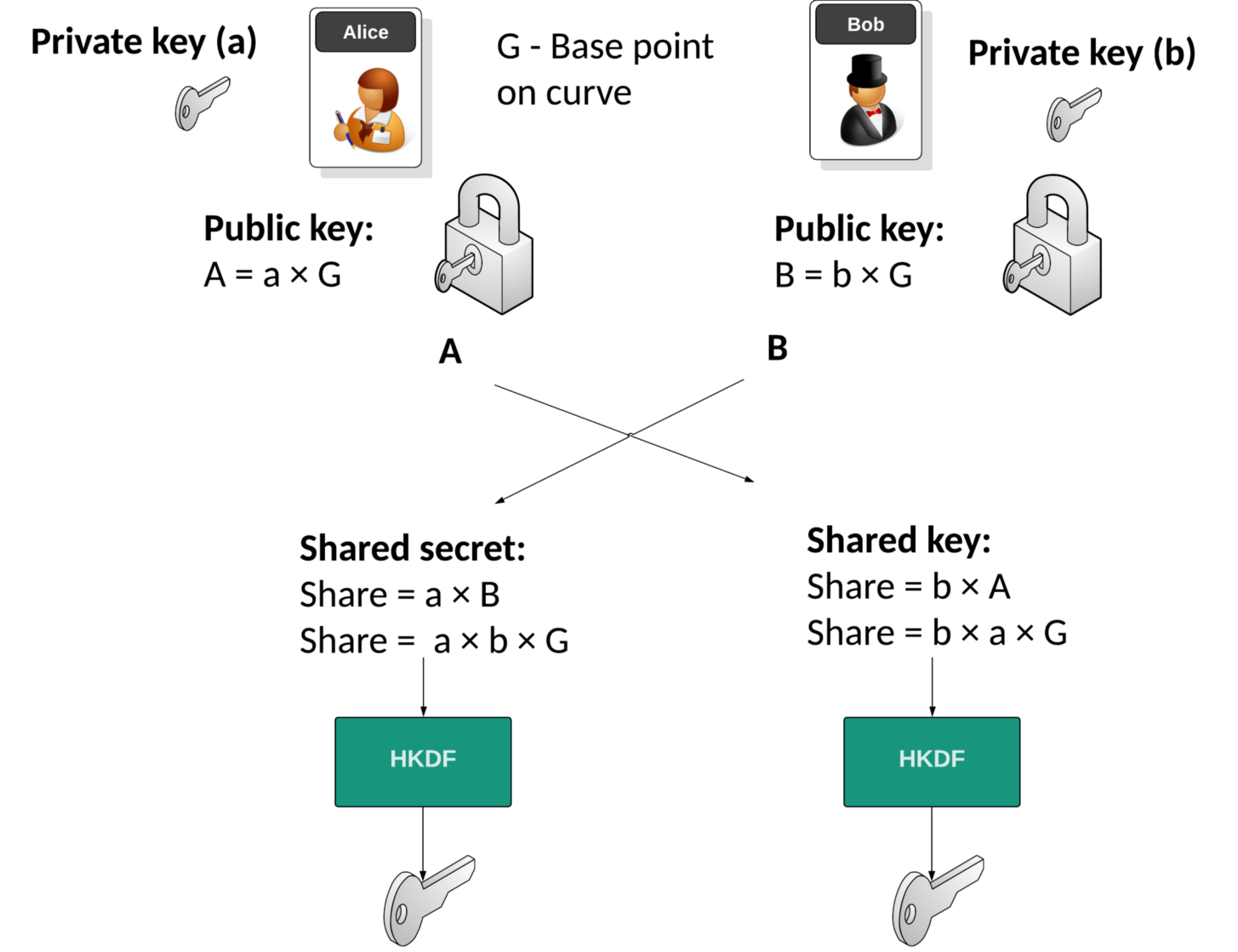







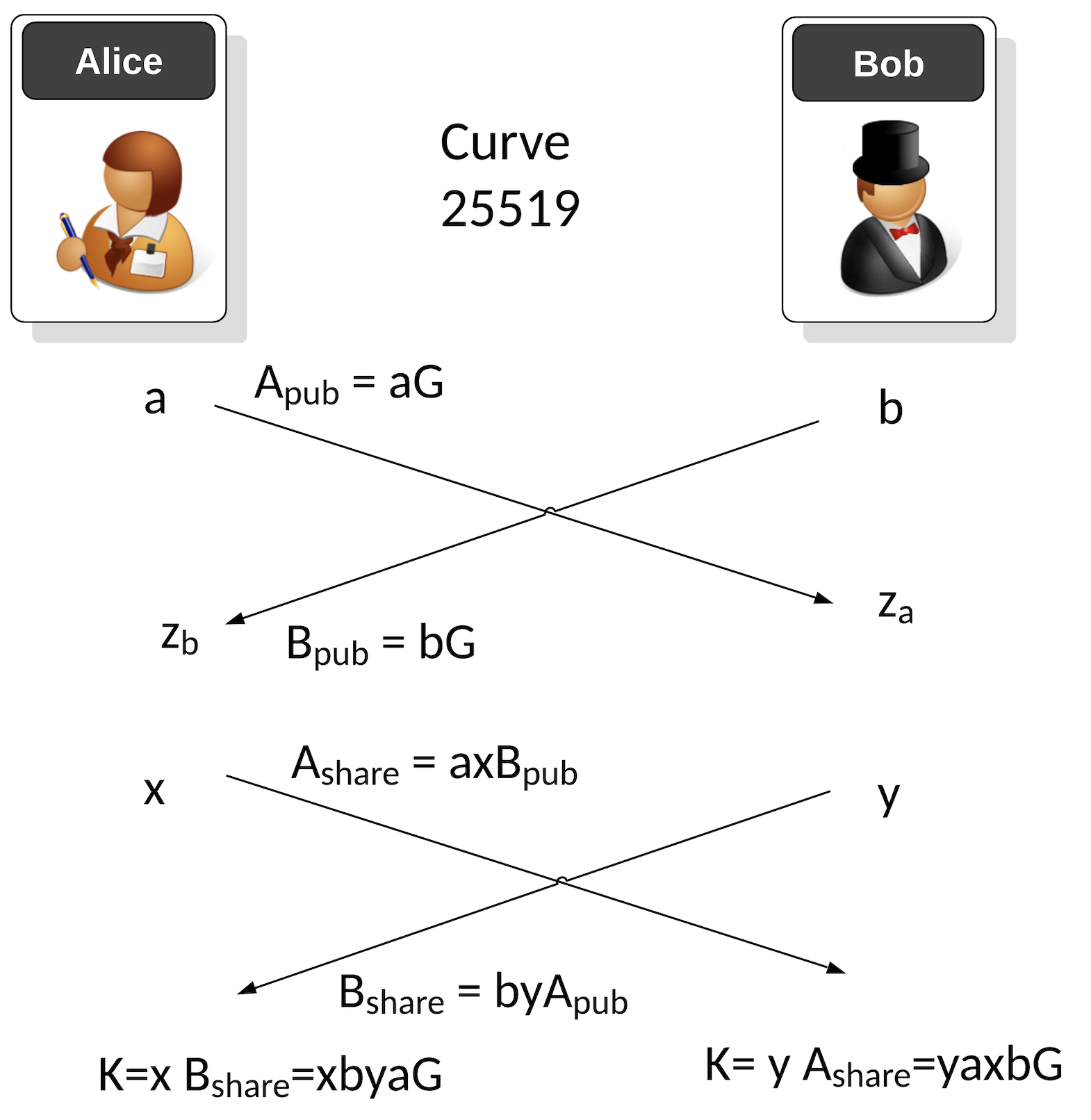

![PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/de032e79b6116aeb3efc26de258903d6fdc24a08/1-Figure1-1.png)